Big Data

Multi-Cloud IT Executive Buyer's Guide
Intentionally establishing a multi-cloud strategy is a powerful way to modernize your IT infrastructure...

A Public Sector Guide to Getting More From IT
The Covid-19 global pandemic has had a huge impact on organisations of every size and in every sector,...

97% of data sits unused by organisations
Data has the capability to transform your business, but only if it's collected and processed in the right...

The Road To Digital Experience Success
The world of work is not changing. It has already changed. Firms that have not boarded the ship need...

8x8: Collaboration and AI Take Customer Care to the Next Level
This buyers guide examines the North American contact center market for both premise- and cloud-based...

Cloud: Be Smart
Cloud' is the buzzword for the last few years when it comes to IT infrastructure, isn't it? And it has...

MIT Executive Guide: The AI and Machine Learning Imperative
Companies across various industries are seeking to integrate AI and machine learning (ML) into workflows...

Application Control for Dummies
Application control, sometimes called application whitelisting,is a means for controlling the software...
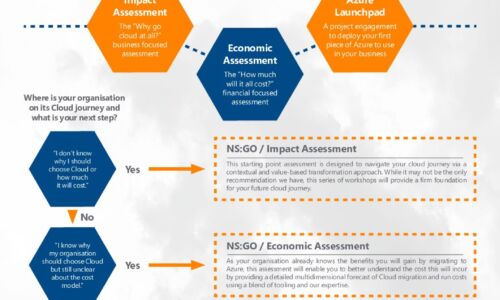
Azure Accelerator kit: Travel in the fast lane with New Signature
At New Signature, we understand that organisations are finding it difficult to start their Public Cloud...

Enabling Great Customer Experience
The blueprint for success starts with a technologyfoundation that links an organisation's front- and...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.



