BYOD

5 Reasons to Make the Shift to Cloud-Managed Networking
Cloud has proven advantages for the enterprise. Modernizing IT with cloud apps, compute, and storage...
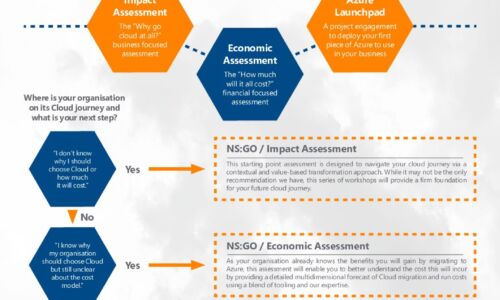
Azure Accelerator kit: Travel in the fast lane with New Signature
At New Signature, we understand that organisations are finding it difficult to start their Public Cloud...

A Simpler, Smarter Approach to Mac Management
Mac devices are making massive inroads across every industry, as more companies offer Mac as a choice....

The Cloud for Better Comms
Technology has helped businesses make some giant leaps forward. But if you can't keep up with it, the...

Top 3 Challenges your Team Faces when Building in the Cloud
And what it means for your business. Today's cloud and security teams are asked to do more with less. Although...

Spotlight: The State of SMB and IT Today
The small and midsized businesses (SMB) continue to be powered by the entrepreneurs who want to build...

Trends in Hybrid Cloud
Cloud computing has helped many enterprises transform their IT practices over the past five years, but...

Mobilising employee productivity in the distributed workplace
Citrix and Microsoft shape modern workplaces that unite the essential elements of today's distributed...

Zero-Trust is the Outcome of Identity-Based Access Control
As the IT landscape evolves, new and more sophisticated cybersecurity threats continue to appear. These...

The Beginner's Guide to Dynamic Case Management
What is dynamic case management? Who is using it and how can it help you prepare for the future of work? The...

Windows Virtual Desktop Jumpstart
Not all applications are web-based or designed to run from the cloud. Many applications still require...

A Five-Step Plan to Move Your Apps to the Cloud
Cloud applications, platforms, and services are changing the way enterprises compete for customers. The...

KuppingerCole Leadership Compass
Leaders in innovation, product features, and market reach for access governance and intelligence. Delivering...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.
