Cloud Computing

A CDO's Guide to Customer Intelligence
To say that the role of the Chief Data Officer (CDO) has evolved quickly is an understatement. Created...

Hybrid Work: Why it's time to move your on-premises PBX to the cloud
For years, the shift to cloud-based communications services was gradual, with some organizations going...

Fast Track to the 5G Edge
As more service providers move toward 5G, they need a scalable, secure, cloud-native infrastructure that...

Time to Consolidate, Not Complicate
Why businesses are consolidating use of a single support solution for both customers and employees. The...

SAP on Private Cloud
Next Level Enterprise with Hyperconverged Infrastructure. Consolidate all aspects of your SAP® landscapes...
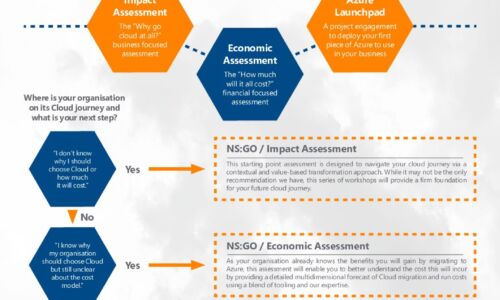
Azure Accelerator kit: Travel in the fast lane with New Signature
At New Signature, we understand that organisations are finding it difficult to start their Public Cloud...

6 Lessons for Cybersecurity Leaders
The state of security is highly adrenalized these days — more so than usual. Years into the deadly...

Facing the future: Digitization in the Public Sector
The continuous improvement with the capabilities of business technologies – like cloud computing and...

All-Flash Buyer's Guide: Tips for Evaluating Solid-State Arrays
Think Flash-First for Primary Storage. The introduction of enterprise-grade all-flash arrays has turned...

The SIEM Buyer's Guide for 2020
In 2020, security information event management (SIEM) solutions will be far more than an information...

Cloud-delivered security for the digital workspace
With the adoption of hybrid cloud and the rise in remote work, traditional connectivity models like VPN...

Enhancing Microsoft Security with HelpSystems Email Security
Learn how HelpSystems Email Security can enhance Microsoft 365. Microsoft 365 offers tiers of security...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

