Cloud

Smart Data Visualization: How to Design Best-in-Class Dashboards
Create stunning data visualizations that tell a story with your data and highlight the Key Performance...

Risk-Aware Data Privacy
Organizations around the world are scrambling to address data-privacy challenges amid workplace shifts,...

Quest® KACE® SMA reduces software license compliance stress
Do you know whether all your software licenses are compliant? Your IT landscape has gotten more and more...

Email Reporting and Remediation
More than ever, attacks seek to exploit human vulnerabilities, not just technical flaws. In most cases,...

Mitigating Information Security Risks in Microsoft 365
Microsoft 365 offers multiple tiers of capabilities that all leverage the cloud to enable professionals...

Tanium Risk Assessment: Know Your IT Risk Score
Assess the risk of all your endpoints against multiple vectors — vulnerabilities, threats, compliance,...
Explore your SASE side
Secure Access Service Edge (SASE), is an architecture that ultimately will integrate networking and network...

The Three Keys to Secure and Successful Cloud Migrations
To make cloud transformations as efficient and successful as possible, companies must remain secure and...

It’s 5 Toughest Work from Home Challenges and How To Solve Them
All of a sudden, you (and everyone else) found yourself working from home (WFH). The one advantage was...
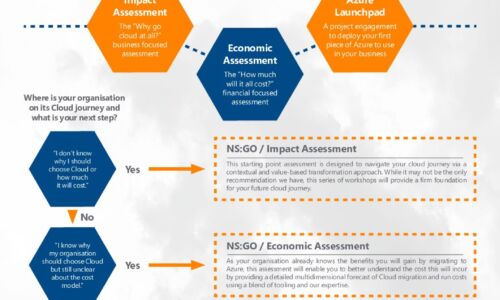
Azure Accelerator kit: Travel in the fast lane with New Signature
At New Signature, we understand that organisations are finding it difficult to start their Public Cloud...

The Anatomy of an Insider Threat Investigation
For decades, perimeter-based security strategies have been the starting point for most cybersecurity...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


