Cloud

M1 quick start guide
Apple will soon fully transition all the Macs in its lineup to the new ARM-based M1 chips and mobile...

Security Control Guide: Hardened Services Guide
System Hardening is the process of securing a system's configuration and settings to reduce IT vulnerability...

WAN & Security Transformation whitepaper
Successful WAN and security transformation requires examining crucial questions: What's the role of a...

GigaOm Radar for Data Storage for Kubernetes
Kubernetes adoption is quickly accelerating, and enterprises are now in a transition phase. In the last...

The Rise of The Machine Economy
Supply chains around the world are experiencing major disruptions as traditional methods of production,...

Top Threat Detections Seen Across Healthcare Organizations
We consider the relationship between Healthcare and Cybersecurity today. How can healthcare security...

Traditional Pentesting: A Turtle Chasing A Cheetah
Why Pentesting Needs to Evolve. Antiquated legacy penetration testing methods fail to catch all the critical...

Business transformation through digital modernization
Amid constant changes, businesses must move rapidly to embrace new work styles. Recent research suggests...
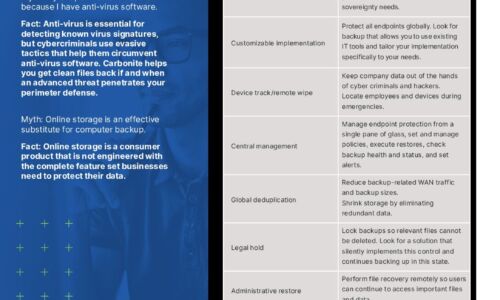
Carbonite Endpoint Protection Myths
Myth: My endpoint data is secure because I have anti-virus software. Myth: Online storage is an effective...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.




