Connectivity

Unified Communications as a Service
As businesses increasingly embrace a cloud-first strategy, many are migrating their most heavily used...

Introduction to AWS Security
Raise your security posture with AWS infrastructure and services. AWS's approach to security, including...
Case Study - Sabiha Gökçen Istanbul Airport
Sabiha Gökçen International Airport has ambitious growth plans. It expects to add a second runway in...

Achieving Data Excellence in Financial Information Management
Financial institutions have accumulated large quantities of valuable data and metadata, but the levels...
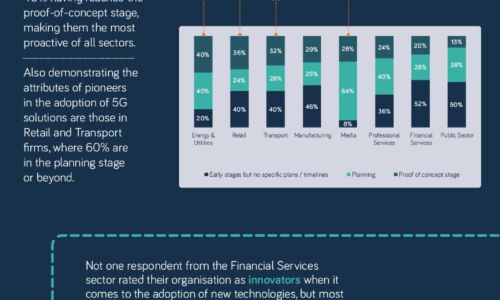
The 5G opportunity within UK industry
Neos Networks research shows that two thirds of organisations expect to have made significant investment...

What is usage data and how do businesses use it?
What exactly is usage data? How does it relate to subscriptions and billing? Why is processing usage...

VMware Cloud Workload Migration Tools
Before starting a cloud migration project, it is critical to understand the strategies and tools available...

Next-Gen iPaaS For Dummies
Digital Transformation changes expectations: better service, faster delivery, with less cost. Businesses...

Understanding Log Analytics at Scale
The humble machine log has been with us for many technology generations. The data that makes up these...

Secure Access Service Edge Palo Alto Networks SASE Comparative Report
This comparative test was commissioned by Palo Alto Networks to evaluate the security efficacy of leading...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.



