Desktop/Laptop OS

SD-WAN Benchmarking Best Practices for QoS by The Tolly Group
While Internet bandwidth increases continually for remote sites, the application demand for that bandwidth...
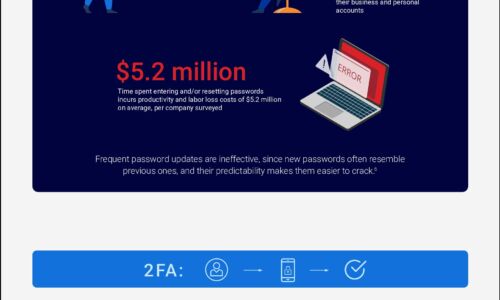
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...

How to Deploy a Comprehensive DevSecOps Solution
Securing DevOps is a complex undertaking, DevOps tools grow and change at a fast pace. Containers and...

Managing Critical Events with BlackBerry Alert
Every day, organizations face risks from natural, technological, and human-caused critical events. While...

The World is Your Workplace: Public Safety Mobile Solutions
Public safety personnel of all types rely on mobile technology to remain connected, efficient and informed....

Become (and remain) the disruptor
If you thought digital disruption was a one-off process to be completed (or resisted), unlocking a new,...

CyberArk 2022 Identity Security Threat Landscape Report
A global report from CyberArk which shows that 79% of senior security professionals say that cybersecurity...

TLS Best Practices
The truth is, a simple lapsed certificate can become a time-consuming headache. Unfortunately, 60% of...

Linux All-In-One For Dummies, 6th Edition
Inside, over 500 pages of Linux topics are organized into eight task-oriented mini books that help you...

Incident Response Use Cases
According to an IBM study, the vast majority of organisations surveyed are unprepared to respond effectively...

Network Security that sets the standard for local government
When it comes to network security, organisations can — and must — learn from the experiences of others....
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


