
Guide to Strengthening Mainframe Security
Successful phishing attacks lead to a loss of control over user IDs, passwords and credentials. Bad actors...

Delivering Real-time Cloud Security Without Trading Off Performance
There has been a long-standing tradeoff between security and performance, and security often gets the...
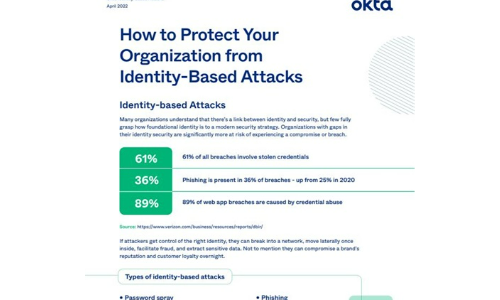
How to Protect Your Organisation from Identity-Based Attacks
Many organizations understand that there's a link between identity and security, but few fully grasp...

Take Control of Security Operations with Consolidation and XDR
The constantly evolving cyber threat landscape and steady stream of cybersecurity technologies designed...

Best-In-Class Email Marketing
Interactions between consumers and brands are increasingly playing out across a wide variety of different...

The state of contact centre transformation in the new digital world
The effects of the pandemic have greatly accelerated the pace of change in contact centres, and there...

CIO Essential Guidance: Intrinsic Security
Despite massive spend to protect enterprise digital assets, security breaches are still on the rise....

Escape the Ransomware Maze
Ransomware is an ever-evolving form of malware designed to steal business-critical data and then sell...

Securing Endpoints Amid New Threats
Giving employees the flexibility to be fully productive while working remotely makes it critical that...

The Behavox Enterprise Conduct And Risk Report
The Behavox Enterprise Conduct and Risk Report, which surveyed 3,000 corporate professionals and 600...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.



