Embedded Systems

Taking Control of Your Office 365 Data
Modern software-as-a-Service (SaaS) applications such as Microsoft Office 365 can offer several advantages...

PHP, MySQL, & JavaScript All-in-One For Dummies
Get the basics on four key web programming tools in one great book! PHP, JavaScript, and HTML5 are essential...

The Zero Trust Guide To Remote Worker Security
With the recent increase in the number of employees working from home as a result of the COVID-19 outbreak,...

Brian Madden Insights: From Desktops to a Digital Workspace
The first 20 years of 'end-user computing' (EUC) were really about desktop computers sitting on users'...

NoSQL for Dummies
This easy to read guide to NoSQL databases provides the type of no–nonsense overview and analysis that...

Report: ICS/OT Cybersecurity 2021 Year in Review
Dragos is excited to present the fifth year of the annual Dragos Year In Review report on Industrial...
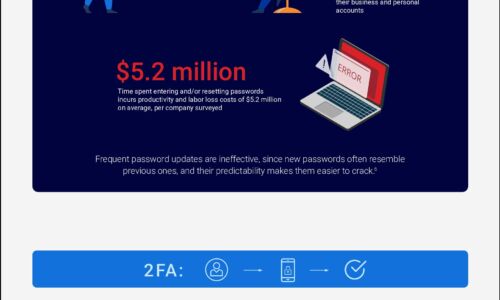
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...

AI-Driven Threat and Incident Prevention, Detection, and Response
Traditional cybersecurity, for lack of a better word, is dead. The proliferation of mobile technology...

Veeam + Microsoft Combine to Offer Rapid Time to Value
IT leaders are discovering that default data protection schemes are not as robust as they desire. As...

Endpoint security versus productivity in utilities: a false choice?
Utility companies are often targeted because they can be used so effectively as phishing lures, as they...

The New Reality: Bring Order To Chaos With Unified Endpoint Security
Chaos and confusion dominated the enterprise cybersecurity landscape even before the COVID-19 pandemic...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


