Endpoint Security

BlackBerry Guard: Solution Brief
Many businesses overlook or underinvest in managed detection and response (MDR), a critical aspect of...

Rackspace Fanatical Support for AWS
As organizations move their workloads from traditional data centers to AWS, IT security paradigms are...

The Evolving Workplace: Everything as a Service
Innovations in technology disrupt traditional business models. One way companies are already starting...

Privileged Access and the Impact of Pass the Hash Attacks
The goal of this survey was to capture hard data on current experiences, trends and approaches to Identity...

Delivering Fast and Secure Enterprise Applications
Adopting a zero trust security model — authenticating and authorizing every request, device, and user...

A CIO's Guide to Accelerating Secure Digital Transformation
Cloud transformation is imperative, and it's the CIO who is under pressure to make sure the business...

Securing Endpoints Amid New Threats
Giving employees the flexibility to be fully productive while working remotely makes it critical that...

Artificial Intelligence: The Smarter Approach To Information Security
The news headlines are replete with stories of devastating data breaches, compromising the personal and...
Transforming the SOC: Building Tomorrow’s Security Operations, Today
When you think of a security operations center (SOC), what comes to mind? Is it an organized team of...
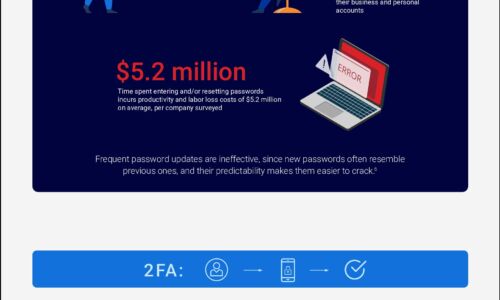
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...

Build better endpoint security to protect your entire network
The threat of a serious cyberattack is nothing new — but the situation just keeps getting more complex....

Open Channels, Hidden Threats
How Communication and Social Media Tools Are Changing the Insider Risk Equation for Compliance, IT and...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

