ERP

Ransomware Survival Guide
Be Ready for Ransomware Ransomware is an old threat that just won't go away. While overall volumes have...

CISO's Playbook to Cloud Security
To secure enterprise assets in the cloud, CISO's must address several new challenges unseen in traditional...

Five Best Practices for Mitigating DDoS Attacks
Distributed denial-of-service (DDoS) attacks remain one of the most effective methods used by cybercriminals...

Building Modern Data Architectures
As the amount of data multiplies, the challenges of managing this data have multiplied, too. Data now...

The Promise of XDR for Effective Threat Detection and Response
In October 2020, the Enterprise Strategy Group (ESG), completed a research survey of 388 cybersecurity...

Confronting the NEW WAVE OF CYBERATTACKS
Like the virus responsible for the worldwide pandemic, email-based cyber threats continued to mutate...
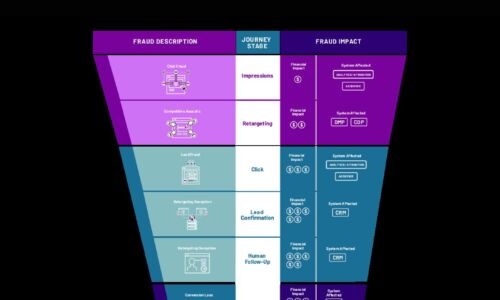
Cybercrime Threatens the Digital Funnel
Cybercriminals are employing new attack methods on new digital surfaces, including digital marketing....

Successfully innovate with AI and ML
Rise above the barriers of implementation Organizations across industries and geographies have long realized...

The 10 Biggest and Boldest Insider Threats of 2019 and 2020
That risk is only increasing in an era of remote working and distributed teams. Without a holistic security...

Moving Endpoint Security to the Predictive Cloud
Traditional antivirus (AV) vendors aren't keeping up with today's threats. They don't protect against...

Brian Madden’s Playbook for Your Journey to the Cloud
Brian Madden, End-User Computing industry analyst and VMware resident expert, explains the big picture...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


