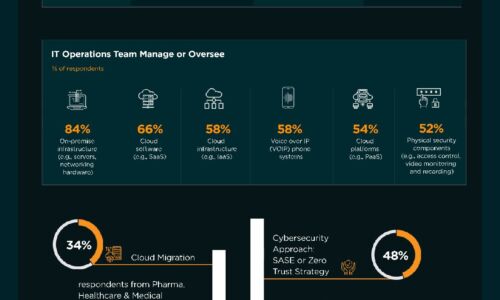
Firewall

Executive Summary: ICS/OT Cybersecurity 2021 Year in Review
In 2021, the industrial community attracted high-profile attention. Major cybersecurity incidents struck...

3 Reasons the Campus Is the Heart of Enterprise Security
Even as digital acceleration continues to transform businesses, the campus remains the heart of the network....

The New Retail Model: A Four-Step Guide to True Algorithmic Retailing
There is one thing successful retailers have in common, particularly in these uncertain times: a firm...

The Ponemon 2021 Cost of Phishing Study
The financial effects of phishing attacks have soared as organisations shift to remote and hybrid work....

Securing Cloud Transformation with a Zero Trust Approach
When it comes to rates of change, cybersecurity has rightly been on the conservative side. Setting up...

Don't Diverge—Converge
Digital acceleration is driving the adoption of hybrid IT architectures. These new hybrid environments...

10 Security Tips for Businesses
SECURITY THAT PROTECTS YOUR BUDGET Vanishing budgets, reckless users, infected machines, unpatched software...

A CDO’s Guide to Customer Intelligence
To say that the role of the Chief Data Officer (CDO) has evolved quickly is an understatement. Created...
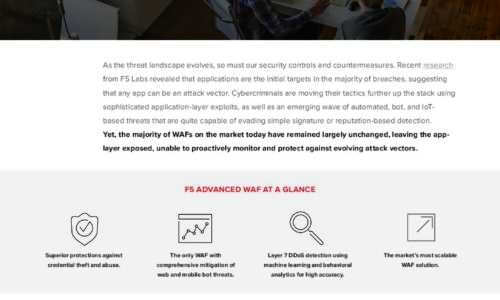
Is Your WAF Keeping Pace with Today’s Advanced Threats eBook
As the threat landscape evolves, so must our security controls and countermeasures. Recent research from...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.