IOT

What is Zero Trust? (Really)
Over the last decade, cybersecurity has been focused on the challenge of securing increasingly vulnerable...

How Virtual Desktop Infrastructure Enables Digital Transformation
Virtual desktop infrastructure (VDI) is a foundational technology that many organizations leverage as...

Big Data for Finance
Across industries, data continues to grow as an extremely valuable resource. This is especially true...

Q4 in review: The latest DDoS attack vectors
2021 witnessed massive DDoS attacks that demonstrate a trend of intensifying cyber insecurity that affected...

New Era In Experience Report
We've all experienced the widespread impact of the COVID-19 pandemic. From a business perspective, the...

Rebellions and rejections report
The global pandemic forced organizations to pivot rapidly from an office-based workforce model to one...

Third-party Risk Management Essentials
From big banks and university hospitals to retail fashion chains and every level of government, organizations...
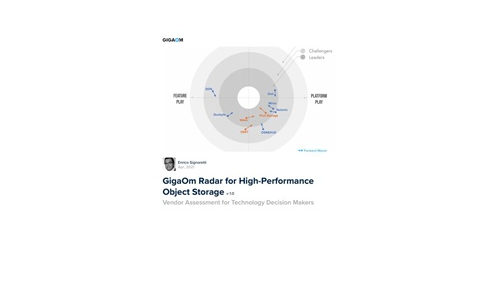
GigaOm Radar for High-Performance Object Storage
For quite some time, users have been asking for object storage solutions with better performance characteristics....

Microsoft Digital Defense Report
Over the past year the world has borne witness to a burgeoning cybercrime economy and the rapid rise...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.




