Network Infrastructure

Deliver secure, immersive gaming experiences with Cloudflare
Between growing their communities, meeting player expectations and defending against attacks, gaming...
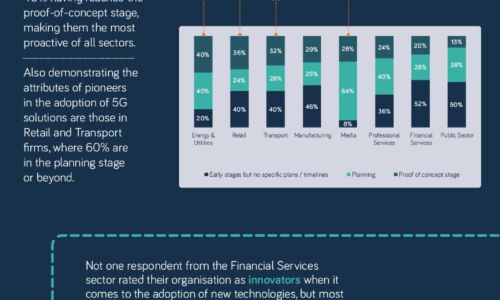
The 5G opportunity within UK industry
Neos Networks research shows that two thirds of organisations expect to have made significant investment...

IDC Whitepaper: Achieving Network Modernization for the Decade Ahead
Every organization is now defined by the digital services it delivers. From engaging customers with new...

5G Is Changing the Game - Right Now. Is Your Infrastructure Ready?
Advanced 5G use cases will require a fundamental change in infrastructure before they can scale. As network...

Insider’s Guide To Choosing a DNS Service
The need that DNS (the domain name system) was created to address seems simple enough: where can I find...

Definitive Guide to Internet Isolation
The traditional approach to cybersecurity has reached its potential, and attackers have learned how to...

Getting Started with SASE
Secure Access Service Edge: A guide to secure and streamline your network infrastructure As enterprises...

Internal Firewalls for Dummies Guide
Organizations can no longer rely on edge firewalls alone to provide network security. Once attackers...

Report: ICS/OT Cybersecurity 2021 Year in Review
Dragos is excited to present the fifth year of the annual Dragos Year In Review report on Industrial...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.




