Network Security

How To Simplify Security With Cybersecurity Mesh Architecture
Networks are becoming increasingly sophisticated and widely distributed, which is making them even more...

LogRhythm for SWIFT Customer Security Controls Framework
Society for Worldwide Interbank Financial Telecommunication (SWIFT) facilitates a huge number of financial...

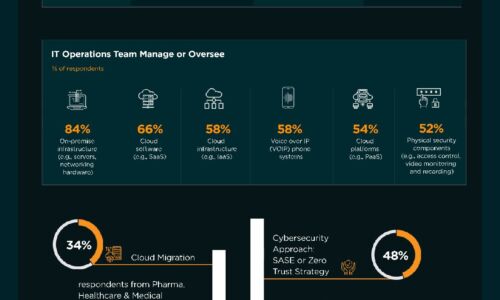
Legal Practice in a Hyper-Connected World
Essential Capabilities and Branding for the New Digital Client. Technology is changing the way that businesses...

5G Technology Transformation Explained
With the 5G era commencing, service providers must ensure that their infrastructures have the cloud-native,...

The 3-2-1 Data Protection Rule and Hybrid Cloud Backup with NetApp
IT teams are under extreme pressure to improve backup, disaster recovery and data protection to eliminate...

Consolidate Cybersecurity Vendors to Accelerate Detection and Response
Organizations of all shapes and sizes are increasingly embracing digital transformation, cloud-delivered...

Penetration Testing For Dummies
Target, test, analyze, and report on security vulnerabilities with pen-testing Pen-Testing is necessary...

The State of Zero Trust Report
The zero-trust network security model has become a pervasive topic for IT professionals. Many organizations...

Making the Grade: End-to-End Security in Education
While students are preoccupied with completing online school assignments and streaming educational videos,...

Top 3 challenges your team faces when building in the cloud
Learn the root causes of the challenges your cloud and security teams are facing and see how these challenges...

DDoS in the time of COVID-19
COVID-19 has caused major disruption to business on a global scale creating the perfect storm for cyber...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.