SAN

Tanium Insights: It's Time to Ditch the VPN for Zero Trust
Many organizations have started adopting zero trust strategies to protect their distributed networks...

Securing Microsoft 365
Few tools are as critical to modern business as Microsoft 365. Unfortunately, the platform's ubiquity...

PCI Compliance Best Practices
The Payment Card Industry Data Security Standard (PCI DSS) has been in place since 2004, with the latest...

Guide to Electronic Signatures
As work evolves to take place outside the four walls of the traditional office, small and midsize organizations...

The top 3 IT pains of the new reality and how to solve them
For those considering a better ITSM solution, there are powerful reasons to think beyond just that singular...

Security and risk management in the wake of the Log4j vulnerability
Security leaders agree: Log4j has irrevocably changed the risk landscape. Get a quick refresher on the...

Selenium Grid Build vs. Buy
Automated testing is essential to software development teams that are moving to continuous integration...

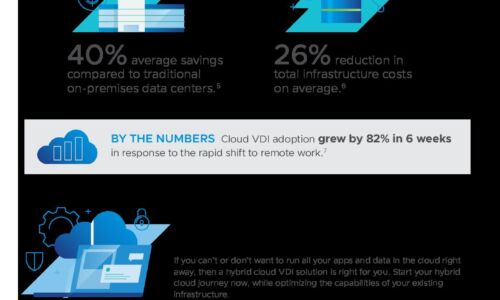
A hybrid vision for the new era of digital transformation
If you are embarking on your digital transformation journey with cloud being an integral part, the best...

Secure Access Service Edge Palo Alto Networks SASE Comparative Report
This comparative test was commissioned by Palo Alto Networks to evaluate the security efficacy of leading...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.