SAN

CISO strategies for proactive threat prevention
Security leaders are under immense pressure to protect their organizations from cyberattacks. But the...

Traditional Pentesting: A Turtle Chasing A Cheetah
Why Pentesting Needs to Evolve. Antiquated legacy penetration testing methods fail to catch all the critical...

Data Governance Is Everyone’s Business
Erwin's contribution to data governance brings IT and business together for a new era in data-driven...

Inside HPC: HPC and AI for the Era of Genomics
2020 will be remembered for the outbreak of the Novel Coronavirus or COVID-19. While infection rates...

The optimized employee of the future
Machine learning is helping businesses push the limits of what's possible. The optimized employee of...

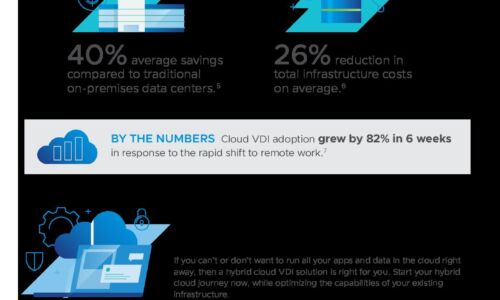
Three Ways to Make Cloud Your Business
The role of IT infrastructure and operations leaders has dramatically changed, and cloud evolution continues...

Threat Intelligence Critical to Cyber Security Protection
Financial services institutions are at the forefront of cyber-attacks and keeping information safe is...

State of Ransomware Readiness Report
2021 has been the year of ransomware. Overall, 80% of businesses around the world have been attacked...

5 Uncomfortable Truths About Phishing Defense
When over 90% of breaches start as phishing emails threats that email gateways miss and other defenses...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.