Security Management

Four Keys to Navigating the Hardware Security Journey
Ensuring enterprise-wide device security requires a shield, or security posture, that follows and protects...

Linux All-In-One For Dummies, 6th Edition
Inside, over 500 pages of Linux topics are organized into eight task-oriented mini books that help you...

Critical Event Management
For today's organizations, the threat of disruptions that critically impact people and business is unavoidable....

Use Case-Driven Cloud Security Evaluator Guide
Researching cloud security? Be sure you evaluate yourself and your vendors on the 6 most common cloud...

The Top 5 Myths of Cloud Security
Hybrid cloud security is a hot topic, especially with the massive growth of public cloud providers like...

Top 3 Challenges Your Team Faces When Building in the Cloud
Today's cloud and security teams are asked to do more with less. Although the capabilities and cost of...

Sotero Data-In-Use Encryption
Though encryption is the most effective way to reduce the probability of a security breach, traditional...
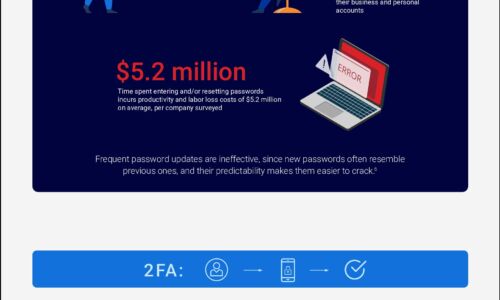
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...

Cybersecurity Insiders: Cloud Security Report
The 2019 Cloud Security Report from Cybersecurity Insiders highlights what is and what is not working...

Top 5 Ways to Simplify Data Protection with Microsoft Azure
Read this white paper to find out five ways that you can simplify data protection with Microsoft Azure,...

Modern upgrade opportunities powered by Veeam DataLabs
With the upcoming end of life of Microsoft Windows server 2008 R2, organizations need to have a plan...

The Survivor's Guide to Building an Office 365 Network
A Microsoft Office 365 deployment can be daunting. From a fast user experience, to a cost-cutting productivity...

Networking and Information Systems (NIS) Directive
The NIS Directive has been designed to work alongside data protection legislation. It will be governed...

Securing Privileged Accounts: Three Steps to Maximize Protection with MFA
Hackers are eyeing your privileged accounts, so you better be using more than 'admin123' to secure them. Multi-factor...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.