Server

Strategies to ensure the success for your identity governance project
Read our ebook to discover clear guidelines you can follow to successfully implement your own identity...

State Of Software Security Report 2019
The 2019 Veracode State of Software Security report represents the 10th version of the report. Much like...
Is Your WAF Keeping Pace with Today’s Advanced Threats eBook
As the threat landscape evolves, so must our security controls and countermeasures. Recent research from...

The Top 10 Reasons to Upgrade to VMware vSphere 7
Customers today demand rapid delivery of innovative applications. To meet those demands, businesses must...

Office Everywhere with Dell Latitude
Introducing a refreshed and most complete mobile portfolio on the planet! Dell's newest lineup of laptops...

Windows Cost Savings Infographic
Save by moving Windows workloads to AWS Companies can lower infrastructure costs while improving performance,...

11 Recommended Security Practices to Manage the Container Lifecycle
This paper details 11 recommended practices for DevSecOps teams needing to move to a more modern application...
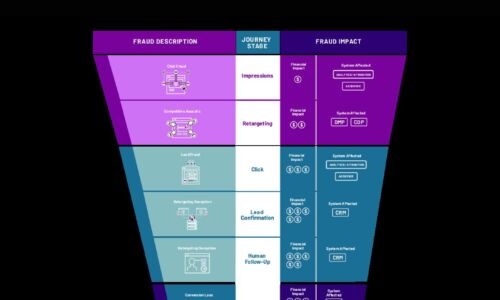
Cybercrime Threatens the Digital Funnel
Cybercriminals are employing new attack methods on new digital surfaces, including digital marketing....

EMA Report: Availability and Buying Options in the Emerging SASE Market
Cloudflare One reviewed as a leading provider of Secure Access Service Edge Gartner's Secure Access Service...

7 Reasons VMware Cloud Foundation is the Premier Hybrid Cloud Solution
Is your IT service delivery future ready? Application and cloud strategies are inextricably linked, and...

The Definitive Guide to Sharepoint Migration Planning
If I've learned anything in more than a decade of working with SharePoint, it's that migration is more...

Protecting Every Edge To Make Hackers' Jobs Harder, Not Yours
Today's users need a network that allows them to connect to any resource from any location using any...

How to Help Prevent Increasingly Rampant Brand Exploitation
Brands have been the unwitting victims of scams since time immemorial. Now, in the age of phishing, it's...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.
