Latest Whitepapers

How Your Business Can Shine Through the Cloud
Over the last decade, enterprise application consumers have been convinced of the lower total cost of...

CIO Essential Guidance: CISO Security Threat landscape
After a year that saw the largest and fastest transformation in work patterns in history, security teams...

Take control of diverse and rapidly evolving enterprise risks
Today's enterprises face diverse and rapidly evolving risks, including expanding regulatory requirements,...

A CIO’s Guide to Accelerating Secure Digital Transformation
Cloud transformation is imperative, and it's the CIO who is under pressure to make sure the business...

Modernize and thrive with Device as a service
Supporting work from anywhere. Addressing evolving security threats. Lowering IT spend. These are the...

How to Build a Cyber-resilient Business Ready to Innovate and Thrive
This eBook discusses if, and to what degree, an organization's adoption of a strong cyber-resiliency...
The Characteristics of Your Future Technology Capabilities
Disruption -- whether big (COVID-19) or small (new start-up competitors) -- has more or less become commonplace...

2018 State of the Enterprise Datacenter
With the Cloud and hyperconverged infrastructure continuing to be adopted by enterprise, it is only natural...

Investa Adds Micro-Segmentation to Security Portfolio
As one of Australia's largest commercial real estate companies, Investa has a powerhouse portfolio worth...
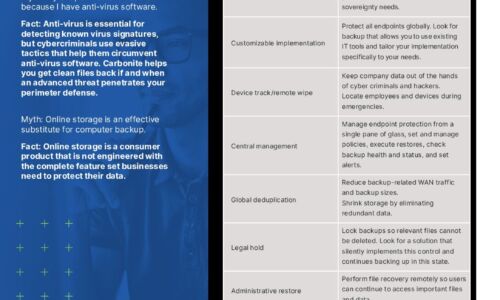
Carbonite Endpoint Protection Myths
Myth: My endpoint data is secure because I have anti-virus software. Myth: Online storage is an effective...

Optimize Your Network for the Distributed Workforce
Ready. Set. Learn: 8 Ways To Optimize Your Network for Remote Workers. Keeping a distributed workforce...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.








