Cloud Computing

Mitigating Information Security Risks in Microsoft 365
Microsoft 365 offers multiple tiers of capabilities that all leverage the cloud to enable professionals...
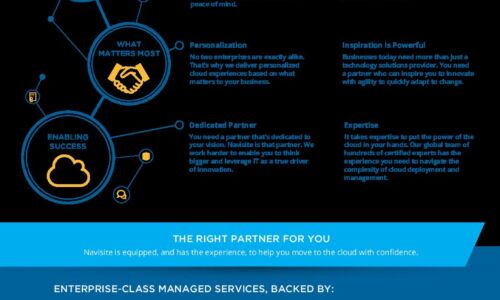
Move to the Cloud with Confidence
Navisite is a leading international provider of enterprise-class managed cloud services. But our story...

5 Usage data software options on the market
If you want to offer usage-based pricing to your customers, there are several IT solutions you can choose....

The Evolution of Employee Experience
Help your organisation adapt to the future of work. When, where and how we work has significantly changed...

The Perimeter’s Gone. Can Your Security Handle It?
Organizations need to shift their security strategy to secure the new ways work gets done. That takes...

It’s 5 Toughest Work from Home Challenges and How To Solve Them
All of a sudden, you (and everyone else) found yourself working from home (WFH). The one advantage was...

Achieving success with your S/4HANA proof of concept (POC)
The value of S/4HANA is now well accepted. During a recent survey, an overwhelming majority of the 480...

5 Steps to Battle Endpoint Cybercrime with KACE
Cyberattacks are increasing across all industries, and cybercriminals are savvier than ever. While the...

An introduction to ITM
As organisations move towards a more distributed workforce, the traditional perimeter of the office network...

Maintaining ‘Business As Usual’ In Unusual Circumstances
The phrase 'business as usual' has a reassuring quality. It represents an ideal state in which the company...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.



