Cloud Computing

Office 365 For Dummies, 2nd Edition (Available For a Limited Time)
If you want to get your head in the cloud and get up to speed on the features in Office 365, you've come...

Cloud Operations eBook
No matter where you are on your cloud journey, AWS Cloud Operations can help you speed up innovation...

How Effective Retailers Balance Customer Engagement and PCI Compliance
For CIOs of retail organizations, compliance with Payment Card Industry (PCI) standards is a top concern,...
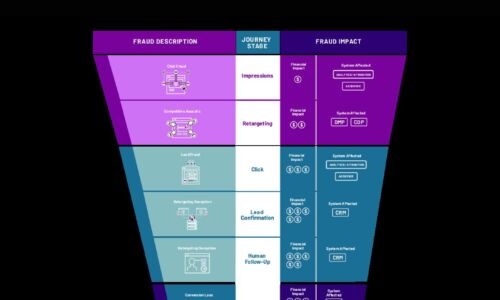
Cybercrime Threatens the Digital Funnel
Cybercriminals are employing new attack methods on new digital surfaces, including digital marketing....

20 Examples of Smart Cloud Security
Smart cloud security provides critical capabilities such as governing access and activities in sanctioned...

Dell EMC PowerStore: Oracle Database Best Practices
This paper delivers guidance for using Dell EMCTM PowerStoreTM T model arrays in an Oracle® 12cR2 (and...

Telstra's Best Practice Guide to Hybrid Cloud
Hybrid Cloud is becoming the strategy of choice for enterprises that want the best of both public cloud...

Identity is Key to Stopping These 5 Cyber Security Attacks
A secure enterprise is a successful enterprise. Security threats are a massive burden for most organizations—but...

Ponemon Cost of Insider Threats Report 2022
External attackers aren't the only threats modern organisations need to consider in their cybersecurity...

Four Data and Analytics Trends to Watch in 2020
The buzz around headline-grabbing topics like machine learning (ML) and artificial intelligence (AI)...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.



