Software

7 Machine Learning Use Cases
Businesses have the opportunity to unlock significant value across the organization with the help of...

MIT Executive Guide: The AI & Machine Learning Imperative
Companies across various industries are seeking to integrate AI & machine learning (ML) into workflows...

The State of Application Security in 2021
Barracuda commissioned independent market researcher Vanson Bourne to conduct a global survey of 750...

Empowering Better Patient Care: Healthcare Mobile Solutions Hotsheet
The cost of healthcare is rising exponentially across the globe. Health services are challenged by a...

A CIO's Strategy Framework for Disruptive Transformation
This is a whitepaper by IDG on behalf of Adobe. Today, we don't know how we will return to our workplaces,...

Customer Workflows Book of Knowledge
The biggest business story of the last year was the impact of COVID-19 on the way we work and live. What...

5 Steps to Battle Endpoint Cybercrime with KACE
Cyberattacks are increasing across all industries, and cybercriminals are savvier than ever. While the...

Aruba’s Roadmap To Hybrid Workplace Success
After the initial network overhaul to enable work from home at the start of the pandemic, organizations...
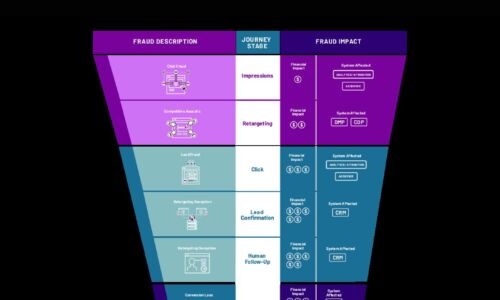
Cybercrime Threatens the Digital Funnel
Cybercriminals are employing new attack methods on new digital surfaces, including digital marketing....
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.




