Endpoint Security

Compromise Assessment Use Cases
With cyber attacks increasing both in quantity and sophistication, how can an organization know with...

Dissecting a Cloud Attack: Securing Azure with AzLog
Microsoft Azure is one of the fastest-growing cloud infrastructure services. Unfortunately, the advantages...

G2 Mid-Market Endpoint Protection Suites Report
Thinking about investing in endpoint protection and want to get a real sense of how different solutions...
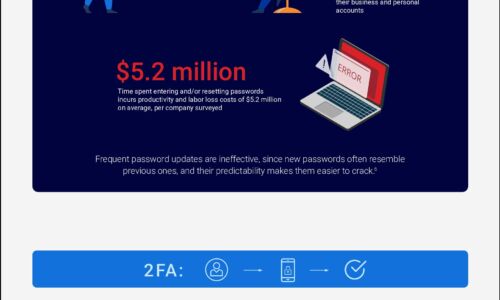
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...

SaaS Security Solution Checklist
SaaS applications have provided tremendous value to end users due to their easy setup and collaboration...

CISSP For Dummies
Secure your CISSP certification! If you're a security professional seeking your CISSP certification,...

3 Ways to Reduce the Risk of Data Loss
Amid the fast-moving digital landscape, security risks are on the rise. People, devices, and objects...

Decoupling security from the network: The evolution of segmentation
You rely on the network to deliver applications. But as IT scales in size, connectivity, and environments...

The SMB Opportunity for MSPs: 2021-2026
According to new research from ConnectWise, MSP industry trends show that SMBs will create over $90 billion...

Aruba Edge-To-Cloud Security
Growth at the edge in the form of remote users and large numbers of new IoT devices has created unique...

CSI Endpoint Security Survey 2022
The unprecedented shift to remote work has changed everything. New data reveals what security professionals...

Future-proofing endpoint management
New devices, platforms, applications, and technologies connecting to the network are overwhelming IT's...

The Top 5 Myths of Cloud Security
Hybrid cloud security is a hot topic, especially with the massive growth of public cloud providers like...

Filling the Gaps in Office 365
Office 365 offers a variety of choices and added functionality making it confusing for IT teams to decide...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.