Software

10 Ways to Fortify Ransomware Recovery Defenses
Ransomware has become a 'cyber-pandemic' that shows no signs of diminishing anytime soon. Your ransomware...

A Modern Approach to Endpoint Remediation
Even with a comprehensive multi-layered protection solution in place, no organization can prevent every...

Hope is NOT a strategy: Secure your business with the Content Cloud
Seems like every week there's news of another cybersecurity breach. Ponemon Institute has found that...
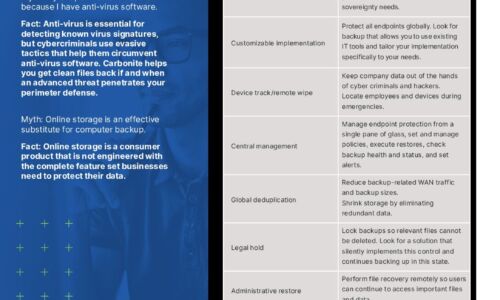
Carbonite Endpoint Protection Myths
Myth: My endpoint data is secure because I have anti-virus software. Myth: Online storage is an effective...

Buyer's guide to all-in-one IT support and management
IT can be hard to manage and support in today's flexible world. Many help desk teams have amassed various...

Protecting the ATM Network with Fortinet
Protecting a network of geographically dispersed automated teller machines (ATMs) is a key challenge...

Multi-Cloud IT Executive Buyer’s Guide
Intentionally establishing a multi-cloud strategy is a powerful way to modernize your IT infrastructure...

Big Data for Finance
Across industries, data continues to grow as an extremely valuable resource. This is especially true...

Reinventing sales: 5 imperatives for the future
The upheavals of 2020 created an opportunity for sales teams to rethink how they operate in a work-from-anywhere...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.




