Software

5G Technology Transformation Explained
With the 5G era commencing, service providers must ensure that their infrastructures have the cloud-native,...

End-point Log management
Deploying a robust log management solution on end-points can be challenging. Monitoring remote end-points...

Understanding Augmented and Virtual Reality
In the book, A Whole New Mind: Why Right-Brainers Will Rule the Future, author Daniel Pink describes...

Stuck in the waiting room
Recent changes in the business world have challenged our assumptions about where employees work, how...

The Forrester Wave™: DDoS Mitigation Solutions, Q1 2021
Cloudflare Named A 'Leader' in The Forrester Wave™: DDoS Mitigation Solutions, Q1 2021 Forrester Research,...

Four Key Considerations for Building the Best Multicloud Architecture
As cloud architects move more workloads to public and private clouds, hybrid multicloud architectures...
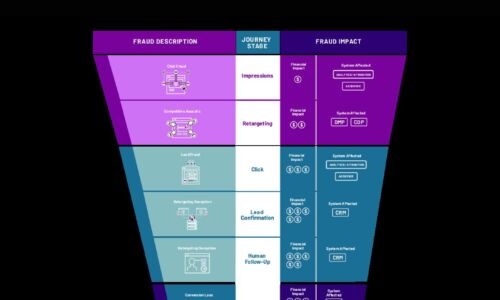
Cybercrime Threatens the Digital Funnel
Cybercriminals are employing new attack methods on new digital surfaces, including digital marketing....

10 Key Questions to Include in Your Vendor Security Questionnaires
Today's perilous cyber world requires you to carefully check your vendors' security posture – typically...

A Buyer’s Guide to Audit Management Software
For today's internal audit teams, the audits themselves are only one part of a growing scope of responsibilities. Executives...

Enterprise Backup and Recovery Made Easy
Protecting enterprise data in a complex IT environment is challenging, time-consuming, cumbersome and...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.